How to manipulate payload data sent through a packet using ICMP ping?

ping is just to check network connectivity! But what actually it is and can be done with the tiny looking ping command?🤔
Published on September 27, 2020 by Suraj Kumar
ping hping3 payload secforge
6 min READ
Ping command
ping is the primary TCP/IP command used to troubleshoot connectivity, reachability, and name resolution.
The ping command sends a request over the network to a specific device. A successful ping results in a response from the computer that was pinged back to the originating computer.
According to the author, the name Ping comes from sonar terminology.
In sonar, a ping is an audible sound wave sent out to find an object. If the sound hits the object, the sound waves will reflect, or echo, back to the source. The distance and location of the object can be determined by measuring the time and direction of the returning sound wave.

When a ping command is issued, an echo request packet is sent to the address specified. When the remote host receives the echo request, it responds with an echo reply packet.
The Ping utility
The ping utility has been incorporated into virtually every operating system with network support. While echo request and echo reply are ICMP messages.
In its simplest form, the ping utility can be run with nothing more than the ping command and a destination. The remote host can be specified either by name or address.
ping 192.168.1.107 # A private addresss in your network
# You can check the networks and ip with
ip a s
# or
ip addr show
# In gui its come pre-installed .If not by installing net-tools you can also use
ifconfig
# To Check IP
ping google.com
ping fb.coom
What if we want to manipulate data through the PING COMMAND.🤔
If we want to send a file from a system to another system over the network using ping command through ICMP tunnel.
hping3
Hping3’s implementation makes the actual construction and transmission of a crafted packet transparent to the user.
The tool easily assembles and sends custom ICMP/UDP/TCP packets, and displays target replies in the same way ping does with ICMP replies.
We need two VM Machine with any linux flavour.
I will be using Fedora OS and Ubunut OS for my demonstation of hping command.
Make sure both the VM should be connected over same network.
I am using a router.
Lets craft some files to be sent over network using hping
Boot up the fedora machine and install the hping command
yum install hping3
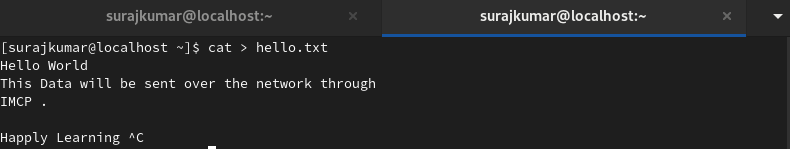
Create a file to be sent over the payload
cat <<EOF >$(pwd)/hello.txt
Hey world this YourName.
I will be sending this data over the network using Internet Control Message Protocol
EOF
Before sending the data we must ensure that both the system should be connected over the bridge / Host only network.
It should be able to ping each other.
IP of both the VM.
ifconfig # If not installed you can use
ip addr show # if Ifconfig does not work
ip a s # Also a alternative to check the ip


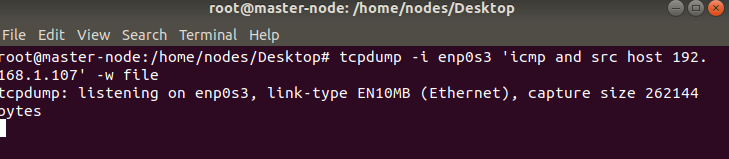
Enable tcpdump on the ubuntu system so that it can recieve the packets.
tcpdump -i enp0s3 'icmp and src host <Your address here>'
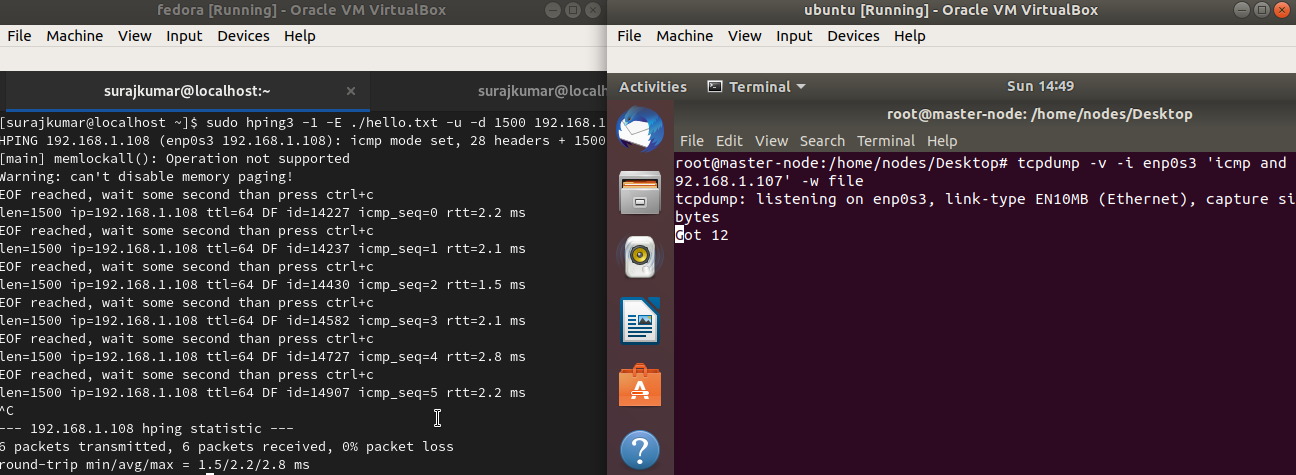
Now send the file over the network using hping3 and receive the packets using tcpdump
# On fedora Machine
sudo hping3 -1 -E ./hello.txt -u -d 1500 192.168.1.108
# -1 is used to let hping3 now we are going to send ICMP request.
# -E is used to tell hping3 the file we are going to sent
# -u Please indicate the user when the tansfer is complete
# -d It is to indicate the size of the packet.
# When its done you will see the EOF reached in the sender system
ctrl+c
# To stop it sending the data further.
# On ubuntu machine
sudo tcpdump -v -l enp0s3 'icmp and 192.168.1.107' -w file
# When its transmitted through the sender system
ctrl+c # Press to stop
Now to look inside the file you must install and run the wireshark tool.
sudo apt install wireshark

Now run the file with the wireshark tool
wireshark file&
A GUI interface will be appeared.

We have to do a couple of observations to understand it more better.
Now if we look at the packet list we can see that the ICMP data is fragmented. So why did these packets get fragmented.
So the main thing through which the data gets fragmented is MTU Maximum transfer unit
We can check the MTU of the link by ifconfig command
ifconfig
# In o/p : - enp0s: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ICMP Total header size = 14 byte Ethernet Header + 20 byte IP header + 8 byte ICMP Header = 42 bytes
Maximum ICMP Data in a single packet = 1500 - 42 = 1458 But we are sending ICMP data of 1500 bytes (as set in hping3 -d option)
Now if look at the packet section we can check the that the data is transferred into the ICMP section.
Inside the ICMP section we can check the data section where the original data is recieved.
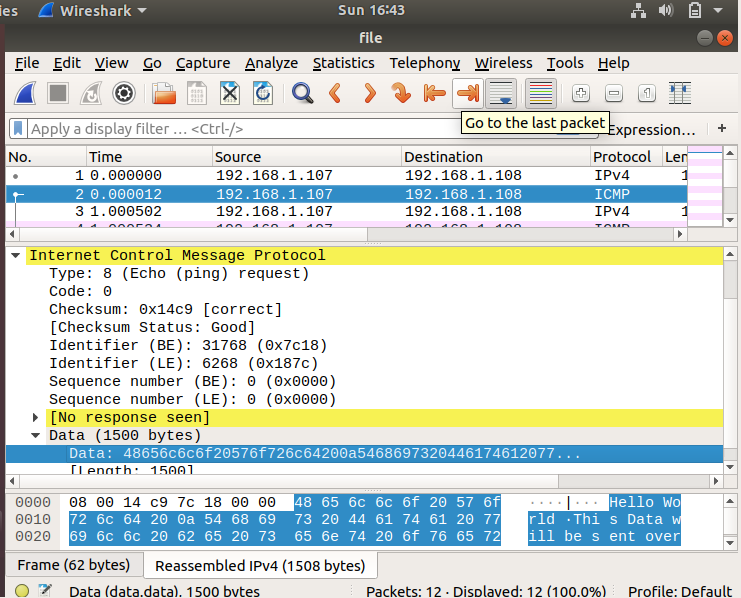
Now to extract the data.data section we can use shark.
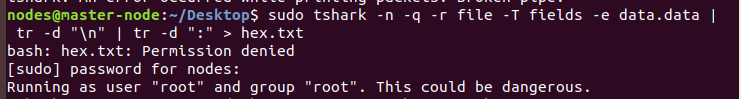
# To extract the hex data we can use a cli tool name shark
sudo apt install tshark
# if tshark is not installed
sudo tshark -n -q -r file -T fields -e data.data | tr -d "\n" | tr -d ":" > hex.txt
# -n is for disable network object name
# -q is for quiet mode
# -r read packet data from filename
# -t Set the format of the output when viweing decoded packet data
# -e add a field to the list of fields to display.
# | send the o/p to the tr Translate or delete characters
# '\n' remove the newline and the ':' from the data we recieved
# saveing the file to hex.txt
Now Visit any website paste the data or upload the hex.txt file and read the data
